Secure ontologies for IoT Devices: a Review and Gap Analysis
Abstract
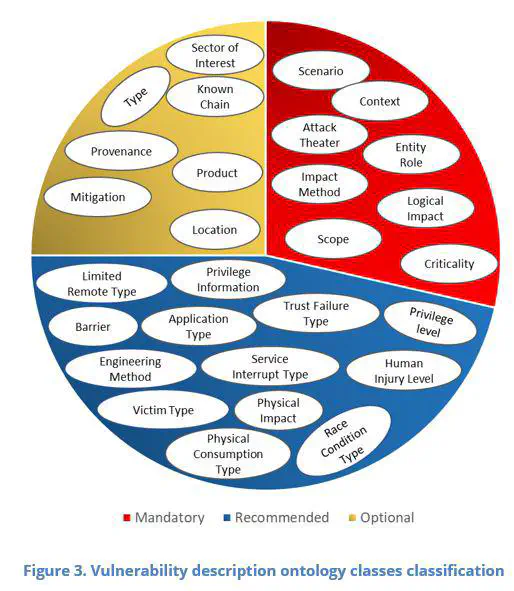
The Internet of Things (IoT) devices are the ears and eyes for Cyber Physical Systems (CPS) and smart applications. The adoption of IoT devices is rapidly increasing both through advanced smart consumers as well as industrial applications such as smart homes, smart buildings, smart mobility, supply chain, and industrial control systems. The IoT devices are used to sense the status of physical environments such as temperature and humidity in a home or supermarket chiller, or vibration in machinery, with sensed data then transported to edge devices and cloud servers for advanced analytics and decisions. Whilst the adoption of IoT devices and digital technologies brings numerous benefits to the CPS in industrial and consumer application domains, they also introduce new cybersecurity risks and challenges. Cybersecurity risk needs to be identified, assessed, and managed with respect to socio-technical aspects and security goals. Most cybersecurity risks increase as more IoT devices are adopted and interact with human operators, users, and environments. This report investigates the use of ontological methods for security modeling of IoT devices, to support the security of IoT devices themselves and their data streams from multiple heterogenous sensors and advanced secure digital twins. Security Ontologies are developed to represent and standardize cybersecurity knowledge through a common vocabulary and machine-interpretable formalism. This will enable cybersecurity experts and software agents to share and communicate IoT security knowledge between each other in the same language. Furthermore, the ontological approaches enable the contextualization and localization of cybersecurity issues through argumentation and machine learning. There are a range of security ontologies and frameworks providing concepts and properties for modeling the security of wireless sensor networks and their data, but none have directly focused on IoT devices. These security ontologies mainly provide very specific classes and properties for application-level modeling and do not follow standardized approaches that enable the reusability and extendibility of ontologies. Existing security ontologies have not focused on the Safety, Resiliency, and Availability concerns of IoT devices which are vital for internet/intranet connected Cyber-Physical Systems and Critical National Infrastructure. Most importantly, these existing security ontologies have not considered the limited computing power of IoT devices. In this report, we analyze the ontological as well as non-ontological resources for discovering the security concepts, properties, and ontological approaches which support safe and secure IoT applications. First, we investigated how the concepts and properties from security ontologies can be used with the W3C Semantic Sensor Network (SSN) ontology for modeling the security of IoT devices. We also discovered that Asset, Vulnerability, Threat, Impact, and CounterMeasures were the common concepts used in most security ontologies. Second, we reviewed the NIST Vulnerability Description Ontology (VDO) which aims to: (1) standardize descriptions of vulnerabilities in a common format, (2) Automate scoring of vulnerabilities without focusing on any specific device or system, (3) Improve the level of detail in information provided to assist with defense whilst minimizing the increasing risk of cyber-attack and (4) Improve the sharing of information regarding vulnerabilities without any language hurdles. In terms of deficiencies, the VDO has not provided classes that focus on security goals and socio-technical security aspects. The third ontology we reviewed was W3C-Web of Things Security Ontology (WoT-SO), which is still in its initial phase and has not been standardized by the W3C. The main objective of WoT-SO is to represent machine interpretable security mechanisms for Things over the web such as services, data, and devices that use web technologies. The other four reviewed security ontologies include reference ontology for IoT Security (IoT-Sec), STAC ontology, Cybersecurity Vulnerability Ontology (CVO), and Industrial Control Security and Threat Modeling Ontology (ICSaTMO). All four of these security ontologies have used similar concepts and properties except ICSaTMO, which focused on safety, the risk of vulnerabilities, and potential cyber-threats to the industrial controls connected to digital technologies and devices. The challenges posed by IoT devices’ security to connected CPS and digital twins raise new research opportunities. Based on the analysis of existing studies, we can report that there is a research gap in many aspects of cybersecurity for IoT devices. For instance, there is a need for ontological frameworks and methods which focus on security data interoperability and integration for secure CPS and secure digital twins, resiliency modeling for IoT devices, and secure APIs for interfacing with the digital as well as physical part of digital twins. Ontological methods can be explored to grant a socio-technical lens of IoT device security, deducing complex relationships between IoT devices and environments to choose the most appropriate countermeasure against cyber-attacks, mapping IoT device security controls to achieve desired security goals, and argumentation for context-based access and control of IoT devices.